Hi Everyone,
In this issue we guest a special guess - Colin Crowden. He will take over the OSINT & Tools section!
We've known each other since last summer's cybersecurity program. For those who missed my Wednesday LinkedIn post, here's a quick intro.
Colin is Head of Digital Intelligence at Global Protect, an OSINT analyst and digital intelligence leader, known for his role on Channel 4’s Hunted and a career spent operating in some of the world’s most hostile environments, from UK Defence to global corporate security. With roots in counter-terrorism and anti-corruption, he pairs sharp analysis with creative problem-solving; whether building tools, leading intelligence teams, or mentoring talent. Colin now helps organisations harness OSINT to stay ahead of emerging threats.
Colin also recently started an OSINT blog/newsletter (The OS), so show some support by signing up or follow along!
Let’s check out the latest news roundup.
Cybersecurity News
CVE Funding Ends: MITRE has announced that funding for the CVE and CWE programs will expire on April 16, 2025. The CVE database is a vital resource for vulnerability management - may go offline. Historical data will still be accessible via GitHub. While the U.S. government is working to support the program, its future remains uncertain. More details: MITRE Contract Info.
EU Launches EUVD – A CVE Alternative aligned with NIS2
In light of a possible CVE shutdown, the EU has introduced the European Vulnerability Database (EUVD). Led by ENISA, it offers a regional platform for reporting and tracking vulnerabilities—enhancing coordination and transparency across member states.Other initiatives: GCVE (now supported by vulnerability-lookup) and the upcoming CVE Foundation (the domain was registered 15.04.25) - info from one of Polish cyber fellows
4chan Hacked, Source Code Leaked: The infamous imageboard 4chan has been hacked, with its source code reportedly leaked online. A user from rival forum Soyjak.party claimed responsibility. Find out more - an interesting thread on X.
Vulnerabilities & Exploits & Hacks
Russian phishing hits Europe: A new phishing campaign targeting European government & military organizations has been uncovered by Google Threat Intelligence Group, attributed to the Russian espionage actor UNC5837. Find out more.
Multi-Stage Phishing Attack Exploits Gamma (an AI-Powered Presentation Tool): In a new campaign, attackers exploit the AI-based tool Gamma to deliver polished phishing links disguised as Microsoft SharePoint logins, leveraging users’ unfamiliarity with the platform to bypass detection and steal credentials. Find out more.
Threat Hunting & Malware
Chinese BRICKSTORM Malware Variant: Belgian security experts from the NVISO have discovered a Windows variant of the BRICKSTORM malware linked to Chinese espionage group UNC5221. Find out more.
SpyAI Malware uses Slack and GPT-4 for Visual Recon: New malware "SpyAI" captures full-screen screenshots, exfiltrates them via Slack, and uses GPT-4 Vision to analyze and reconstruct daily user activity. Find out more. (Github)
📰 Reports
Espionage & Counterintelligence
Sweden Warns of Russia’s New Sabotage Tactics: Sweden’s Security Service reports a disturbing shift in Russian espionage strategy: recruiting individuals with substance addictions for sabotage missions across Europe. Find out more.
Japan Eyes Geospatial Intel Partnership with Ukraine: While Japan strengthens its intelligence ties with Ukraine, a Tokyo-based company considers launching a strategic monitoring platform in the region. Find out more.
Czech Republic uncovers longtime Russian Intelligence Asset: Czech authorities identify a key collaborator of Russian military intelligence. Belarusian journalist Natalia Sudliankova and officer Alexey Shavrov have been ordered to leave the country. Find out more.
Pro-Kremlin Politician Takes Power in Abkhazia: Badra Gunba, backed by the Kremlin, is inaugurated as president of Abkhazia. Russian presidential aide Sergey Kiriyenko, overseeing Abkhazia affairs since January 2025, attended the ceremony. Find out more.
Crypto
My friend 👋 from FIU Sri Lanka built a simple, educational tool to visualize TRC-20 blockchain transactions (tokens running on the Tron blockchain, similar to Ethereum's ERC-20 standard) — check it out: https://trc20.lk 🚀
🔍 Key Features:
Real-time TRC-20 transaction data via TronGrid API
Visual dashboards for easier blockchain analysis
Perfect for students and beginners in blockchain tech
Lightweight, non-commercial tool focused on accessibility and clarity
SOCMINT
TikTok “Cheat Codes” for Evading Moderation
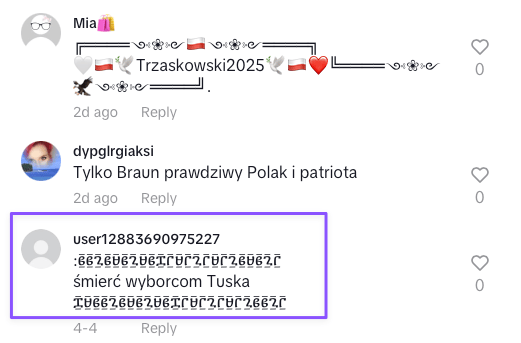
While analyzing the TikTok campaign of one of the presidential candidates in Poland, we at frontstory.pl came across a recurring pattern: under nearly every one of his videos, there were comments filled with strange-looking symbols, posted by supporters of rival candidates.
Below is an example from April 4, 2025, containing the phrase: “death to the voters of X.”
These strange symbols are actually Amharic, a Semitic language primarily spoken in Ethiopia and written in the Ge’ez script. TikTok’s AI-driven content moderation doesn’t recognize it — and the comments remain visible.
In 2024 comments look like that, still it’s a Amharic languages.

Other techniques used to bypass moderation:
Inserting non-alphabetic characters (such as @, #, $, , _) or spaces between letters, e.g. “Ples+in1ans” & “terr0rist+s”.
Using Unicode characters and decorative fonts – tools like LingoJam allow users to generate stylized text that may bypass keyword filters.
Eplacing words with emojis – for example, the emoji 🐕 (terrier breed dog) is used instead of the word “terrorist”, and 🎻 (violin) instead of “violence”.
Euphemisms and “algospeak” – users invent alternative words or phrases that aren’t on moderation blacklists but sound similar or are understood through context.
Examples include:
– “unalive” instead of “kill”
– “mascara” used as a euphemism for “sexual assault”
OSINT Guest Section
OSINT Tools and Websites for Combatting Disinformation
Disinformation poses a significant threat, influencing public opinion, compromising security, and eroding trust. As misinformation tactics evolve, OSINT professionals require increasingly sophisticated tools to detect, monitor, and mitigate false narratives. Below are some of the latest and most effective OSINT tools and websites available to professionals working to counter disinformation.
Tools recommend by Colin
NewsGuard: it’s employs journalists to provide reliability ratings for news websites, assessing transparency, credibility, and accuracy. By using colour-coded ratings, OSINT analysts can rapidly determine the reliability of sources, helping to quickly identify and dismiss questionable information.
Bot Sentinel: Bot Sentinel utilises machine learning to detect and analyse fake or troll-driven accounts on platforms like Twitter. It helps OSINT professionals distinguish authentic conversations from automated propaganda, significantly reducing the impact of coordinated misinformation campaigns.
Hoaxy: Developed by Indiana University, Hoaxy visualises the spread of misinformation and fact-checking efforts on Twitter. By mapping interactions, it provides insights into how false information proliferates, helping OSINT teams target influential nodes that amplify misinformation.
InVID Verification Plugin: InVID is an essential tool for verifying and debunking multimedia content. Designed as a browser plugin, InVID simplifies the verification of images and videos through reverse image searches, metadata extraction, and forensic analysis techniques. It significantly reduces the time required to validate content authenticity.
Vastav AI: Vastav AI, developed by Zero Defend Security, is a powerful deepfake detection system designed to verify digital media authenticity. It accurately detects AI-generated videos, images, and audio content with a high degree of reliability, enabling OSINT professionals to rapidly identify manipulated media used in disinformation campaigns.
Leveraging these cutting-edge OSINT tools empowers professionals to effectively counter the rapid spread of misinformation. Staying abreast of developments in OSINT technology and continuously updating methodologies ensures a resilient response against evolving disinformation threats.
Read Colin’s latest articles related to this topic:
Automated OSINT source evaluation workflow - Quick guide for busy analysts. Check it here.
A downloadable, step-by-step guide to building your own disinformation counter-measures workflow. Check it here.
Google Updates
Google Launches A2A Protocol to Let AI Agents Collaborate Across Clouds and Platforms: Google’s new Agent2Agent (A2A) protocol enables seamless communication between AI agents, with support from over 50 partners including Salesforce, SAP, Atlassian, Box.
Gmail Overhaul Forces 3 Billion users to rethink privacy amid rising AI-Powered Phishing Threats: Google's latest Gmail update introduces AI-driven search and streamlined encryption, prompting users to reassess privacy settings as sophisticated phishing attacks become more prevalent.
Darknet
Cracked Forum Returns under New Domain: Recently seized by law enforcement, the notorious Cracked forum is back online—looks like a honeypot.
Upcoming CyberSec / OSINT Events
Free
OSINT Webinar - Social Media Intelligence... without Logging in with Griffin and Micah – hosted by My OSINT Training - April 23, 2025 – YouTube, 12 PM ET.
Cyber Resilience Conference – April 23, 2025 – Mechelen, Belgium. Register here.
UK CyberWeek: Expo & Conference – April 23–24, 2025 – Olympia, London, UK. Register here.
SANS Cybersecurity Leadership Summit (Virtual) – April 24, 2025. Link.
Paid
Osintomatico 2025 - OSINT Spanish Event - Workshops – May 12–14, 2025 & Conference – May 15–17, 2025 – Madrid, Spain. Link.
I was at this event two years ago and highly recommend it!
x33fcon – June 12–13, 2025 – Hybrid: on-site in Gdynia, Poland, and online with live streaming. Link.
Disinfo2025 – October 15–16, 2025 – Ljubljana, Slovenia
Early bird tickets available until the end of May. Link.
🙃Bonus
Someone in my network - StealthMole is looking for a remote OSINT analyst to track dark web threats, earn up to $6K/month part-time, and possibly grow into a full-time role— apply especially if you're from Indonesia, India, Pakistan, Iran, Bangladesh, or Malaysia. More info here. (docs)

